Disclaimer
I am definitely not the one who managed to get ‘first blood’ for this badge (mad respect to @elma for getting there first), but maaayyyybeeeee I might be the first to do a writeup on this? I’m definitely not so sure about this but it will be my first ever writeup for a hardware badge.
Prologue
For years I’ve been an avid fan of conference badges but I did not end up solving them due to my self-confidence (and lack of time) to attempt it, because I really had no idea how to start off.
For this year’s SINCON badge, it was the iconic Dragon Playground (that I used to see in old HDB areas back in my younger days), which looked pretty neat and slick:

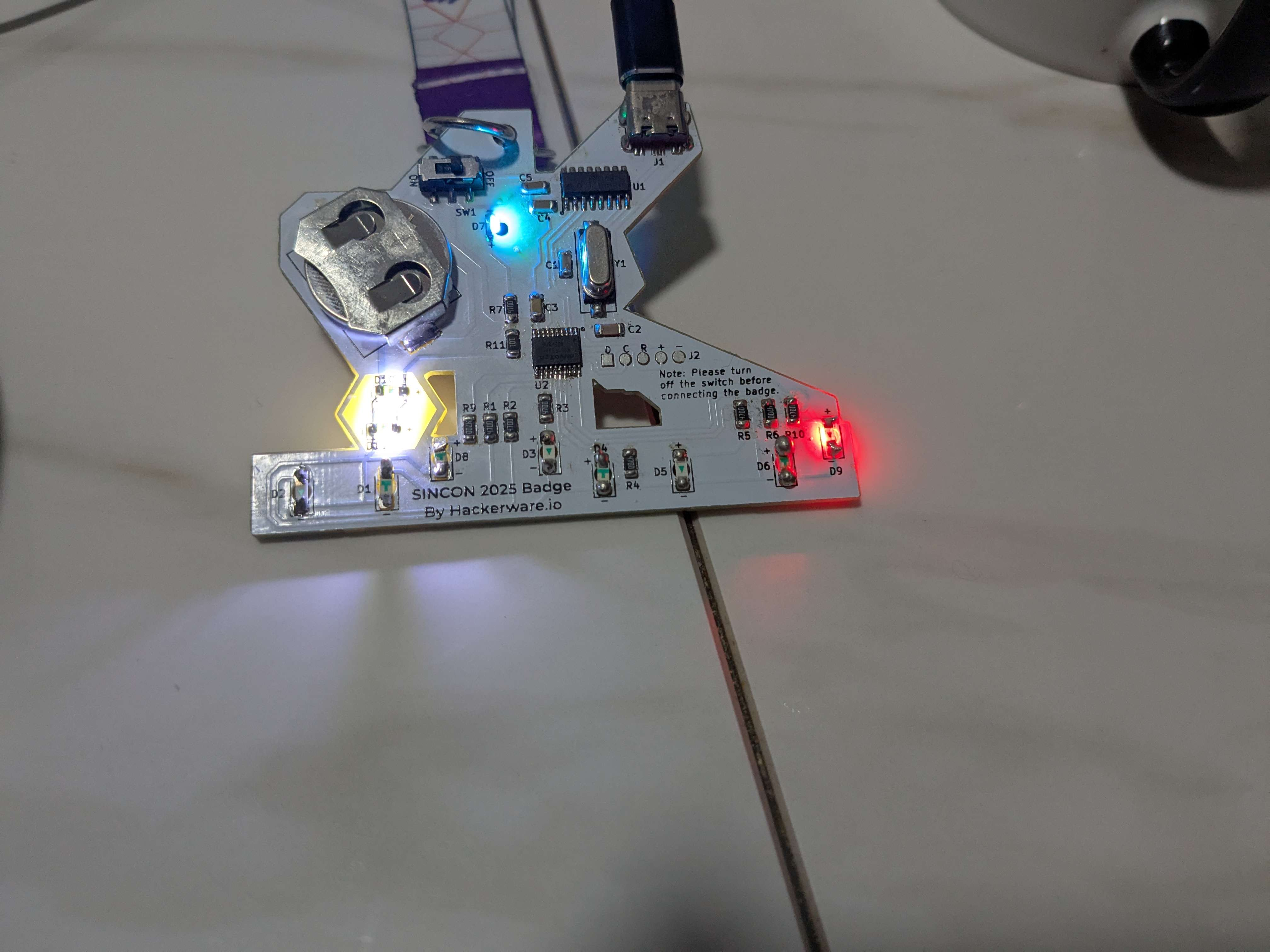
I can safely say that I now have soldering hardware experience as it was pretty fun to solder my 8 LED lights on the badge, at the expense of accidentally inhaling a bit of the smoke (note ah, the photo isn’t me):

To light up the 8 LED lights, you will need to solve all 8 CTF challenges that are located within the badge’s firmware, as seen in the Arduino output:
For more details regarding the orientation and setup, you can look up here (which was pretty easy to set up to be honest): https://www.hackerwares.in/sincon2025.
Challenge Solutions - Quick Summary
I was kind of expecting more of the firmware reverse dumping stuff like what I saw in the STANDCON 2025 badge, but here’s the quick overview of all the challenges and its solutions (not gonna put the challenges here. if you want it, go get the badge at next year’s SINCON):
| Challenge | Solution (or pretty much the approach to do it) | Flag |
|---|---|---|
| 1 | Bacon Cipher | sincondragon |
| 2 | Elder Futhark alphabet system | sinconparc |
| 3 | merge partial qr code images (one inverted), followed by ROT-13 | t0a-p4y0h |
| 4 | Load gerber file into a gerber file viewer online, followed by Rail Fence / ZigZag decoding (Key: 3) | dr4g0n-c1ty |
| 5 | Steganography of wav file (with password protected file), using rockyou.txt for encoding. Tool to use was ‘stegseek’ to crack the password for the .wav file. | bre4th-f1r3 |
| 6 | Semaphore flag decoding | dr4g0n-fru1t |
| 7 | First character shows the actual character of the flag. Subsequent digits show the character placement of the flag. | dr4g0n-p14y |
| 8 | Pretty much a 90s kid if you can solve this :) if not, start texting with a Nokia 3310 phone | drag0n-n3st |
| Personally the tools that I found online were pretty useful to solving these challenges: |
Thoughts
Although the solutions for the CTF challenges were pretty straightforward, I think this was supposed to serve as a quick introduction for newcomers to be onboarded onto hardware hacking in general. Personally speaking, from this experience, I do feel the need to attempt back the STANDCON 2025 Hardware Badge Challenge because of the newfound confidence that I have. Let’s see how it goes!